
03-07-2005, 12:00 AM
|
|
Editor Emeritus

Join Date: Aug 2006
Posts: 5,074
|
|
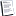 An Oscar Surprise: Vulnerable Phones
An Oscar Surprise: Vulnerable Phones
"Three employees of the company, Flexilis, founded two years ago by four University of Southern California students, positioned themselves in the crowd of more than 1,000 people watching celebrities arrive at the Kodak Theater. John Hering, one of the company's founders, wore a backpack in which he had placed a laptop computer with scanning software and a powerful antenna. ... The Flexilis team said their concern was not with Bluetooth itself, which contains adequate security protection, but with the way the technology has been used by many manufacturers. "We're attempting to raise the level of security in the wireless world to the same standard that is now expected in the wired world," Mr. Hering said."

Photograph by Jim Wilson/The New York Times
The New York Times article [free registration required] seems to have confused the recent T-Mobile network hack with the Bluetooth vulnerability, that was being exposed by Flexilis team. The article does highlight a good point, that Bluetooth protocol on its own does not have any holes, but its implementation by the various phone vendors is not perfect. Wish the article elaborated on what kind of weakness the Flexilis team was looking for. :? The only one I can think of is leaving the Bluetooth on the phone in discoverable mode. But before anyone can access the data on my phone, I will have to accept the incoming request on my phone? Am I missing something?
|
| |
|
|
|
|
|
|
 Similar Threads
Similar Threads









 Threaded Mode
Threaded Mode