
01-17-2005, 10:00 PM
|
|
Editor Emeritus

Join Date: Aug 2006
Posts: 15,171
|
|
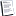 Security Flaw in x50 WiFi WEP Key Store
Security Flaw in x50 WiFi WEP Key Store
"Airscanner discovered a serious flaw in the way the Windows Mobile Odyssey client manages the WEP key information. The Odyssey client included with the Dell X50 stores the WEP keys as plaintext in the registry. The following illustrates: Byte 5 - 9 list my entered WEP keys for each entry."
In other words, if someone gets their physical hands on your x50, it's possible to extract the WEP key without too much hassle. It isn't great that a unit stores WEP keys in plaintext, but on the other hand, WEP isn't that secure anyway. If you're using WEP to secure critical business interests, you should have already developed a migration path to WPA. And for personal use, I wouldn't worry too much about it, since this only becomes an issue if you lose your PDA.
|
| |
|
|
|

01-17-2005, 10:36 PM
|
|
Ponderer
Join Date: Dec 2004
Posts: 55
|
|
What about the Odyssey on the X30?
Why do we need it anyway? It seems I can do everything I do with Odyssey with the native Dell client (WLAN util on the X30).
Amnon
|
| |
|
|
|

01-17-2005, 11:01 PM
|
|
Pupil
Join Date: Dec 2004
Posts: 33
|
|
Quote:
|
Originally Posted by amnon
t seems I can do everything I do with Odyssey with the native Dell client (WLAN util on the X30).
|
Which is probably what most other Axim users do, and thus are not affected by the leak. I also found this information.
|
| |
|
|
|

01-18-2005, 02:22 AM
|
|
Oracle

Join Date: Mar 2005
Posts: 980
|
|
May be I�m wrong but i believe that it�s a bug in the OS and not just of Dell�s PPC. Can any one with WEP check these keys
[HKEY_LOCAL_MACHINE\Comm\<NICCARDNAME>\Parms]
HTCWEPDefaultKey4
HTCWEPDefaultKey3
HTCWEPDefaultKey2
HTCWEPDefaultKey1
|
| |
|
|
|

01-18-2005, 02:34 AM
|
|
Intellectual
Join Date: Apr 2004
Posts: 164
|
|
You'll be at the mercy of the hardware vendor. For instance, most OEM implementations of the Pegasus do, in fact, encrypt the key in the registry. However, someone with time could probably just copy the key anyway.
Odyssey gets used for LEAP, and, for me, non-standard SSIDs. For instance, my SSID contains punctuation of sorts, something that the built-in Windows setup won't allow you to use.
WEP is secure enough for most, as I recall last hearing, to crack WEP, you needed to sniff 10MB worth of data. Still not perfect, but good enough for most. I hear WPA is emerging as the 'one to use' but I don't know much about it.
*Phil
|
| |
|
|
|

01-18-2005, 02:49 AM
|
|
Contributing Editor Emeritus

Join Date: Aug 2006
Posts: 8,228
|
|
Quote:
|
Originally Posted by ctitanic
[HKEY_LOCAL_MACHINE\Comm\<NICCARDNAME>\Parms]
HTCWEPDefaultKey4
HTCWEPDefaultKey3
HTCWEPDefaultKey2
HTCWEPDefaultKey1
|
Those keys do not exist on my WEP protected iMATE PDA2K.
|
| |
|
|
|

01-18-2005, 03:04 AM
|
|
Pontificator
Join Date: Jul 2003
Posts: 1,041
|
|
No problem. Allowing someone to hold my PDA would be the equivalent of allowing them to grab my girlfriend's ass. :evil:
|
| |
|
|
|

01-18-2005, 03:11 AM
|
|
Oracle

Join Date: Mar 2005
Posts: 980
|
|
Quote:
|
Originally Posted by Ed Hansberry
Quote:
|
Originally Posted by ctitanic
[HKEY_LOCAL_MACHINE\Comm\<NICCARDNAME>\Parms]
HTCWEPDefaultKey4
HTCWEPDefaultKey3
HTCWEPDefaultKey2
HTCWEPDefaultKey1
|
Those keys do not exist on my WEP protected iMATE PDA2K. |
Well, I'm sure I have seen that problem before but i can recall in what machine and now that i think about it, those keys are created by the OEM that made the WiFi card.
|
| |
|
|
|
|
|
|







 Linear Mode
Linear Mode

